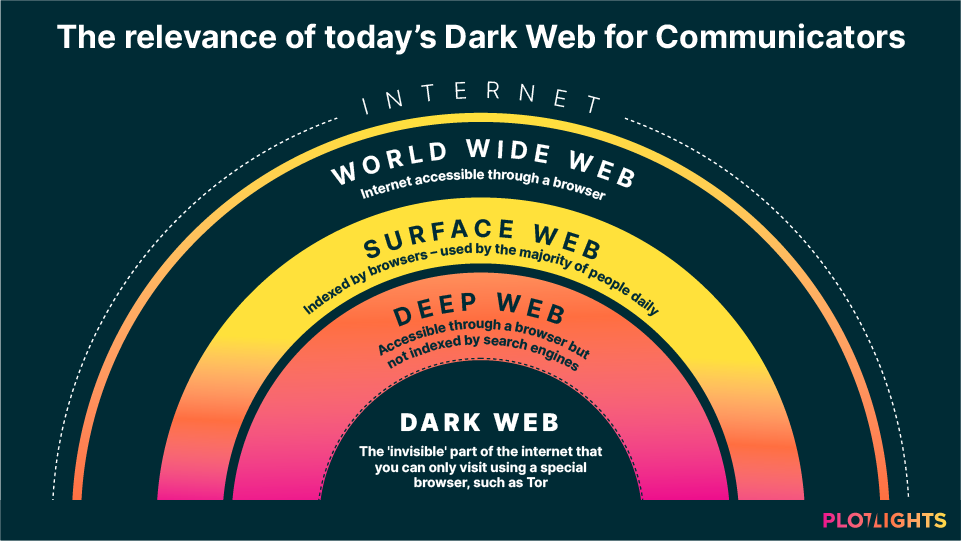
The Internet we all know and use every day makes up only about 4% of what’s available online. The rest of the web, what’s called the Deep Web and the Dark Web, lie well beneath the surface with the latter also being a hub for illegal transactions.
The Dark Web’s anonymized and encrypted nature provides fertile soil for criminals to thrive without having to worry too much about law enforcement. That’s why over the years the Dark Web almost naturally morphed into a marketplace for drugs, weapons, illegal services, and stolen data. With ransomware and generalized malware attacks on the rise and a majority of communication experts reporting that their organizations were the target of cyberattacks, organizations at large, and communicators, in particular, face a unique set of challenges.
In this article, we explore the threats that the Dark Web poses to organizations as well as some dos and don’ts communicators should follow in the event of an attack turning into a crisis.
The Dark Web Today: What’s New and What Changed?
Cyber protection in 2021 is a must-have for all organizations, regardless of size, industry, and geo-location. The increasing number and sophistication of attacks make it crucial for organizations to take preventive steps to establish new security rules and for communicators to put in place effective crisis communication plans.
In Mid-2020, the number of Dark Web forum users rose by 44% spiking during the first COVID-19 lockdown. At the same time, ransomware attacks increased by 148% with phishing attempts growing by more than 660%. According to the Microsoft Digital Defense report, even Internet of Things (IoT) attacks rose by 35% compared to 2019.
The alarming growth spurt of cyberattacks continued in 2021: in January alone, more than 880 million data records were stolen globally which is more than what was stolen throughout the entire year 2017.
To make matters worse, the demand for different kinds of cybercrime has also increased: 69% of recruiting posts on dark web forums look for cyber attackers willing to hack any website as a service. Interestingly, 21% of hackers’ ads center on searching for people willing to obtain client or user databases of specific targets.
Dark Web-Induced Crises: Who’s at Risk?
The growth in the number of data breaches and ransomware-as-a-service cases organized via the Dark Web significantly impacted many businesses, no matter their industry. Historically, it was more individuals falling victim to attacks but lately, cybercriminals increasingly leverage malware to target businesses. Undoubtedly they have more to lose and malicious actors typically also receive a better pay-off.
In June 2021, video game giant Electronic Arts was hit by a data breach. The hackers that infiltrated EA’s network stole some of the source code of its popular football game FIFA 21 and put it up for sale on the Dark Web. Even though EA claimed that the breach did not impact players’ privacy, chances are the company’s revenues and reputation will take a hit. According to Saryu Nayyar, CEO of cybersecurity firm Gurucul the “game source code is highly proprietary and sensitive intellectual property. There’s no telling how this attack will ultimately impact the lifeblood of the company’s gaming services down the line”.
Most of the time malicious hackers infiltrate a network to create or exploit an existing vulnerability to their advantage. But, sometimes, it is the organizations themselves causing cyber incidents unintentionally. And that is what happened to US exercise equipment and media company Peloton. In January 2021, they inadvertently exposed user data to hackers allowing anyone to access Peloton users’ age, gender, location, weight, workout stats, and birthday. What made matters worse for the organization is that, to this day, Peloton has not yet clarified whether anyone maliciously exploited the vulnerability, for example, through mass-scraping such data.
Dark Web Attacks: What Can Communicators Do?
With 60% of small organizations going out of business after a cyberattack, companies must have a holistic plan ready to protect networks, systems, people, and of course the brand’s reputation.
But when a cyberattack hits, here are some useful dos and don’ts:
Do: Leverage Threat Intelligence
Threat Intelligence provides essential information in case of emerging threats or attacks and enables organizations to assess risks, tailor protection strategies, and make informed decisions around network security and the many aspects of organizational cyber resilience. Threat intelligence also provides real-time data, crucial during an attack as it can reveal an attacker’s thought process, motives, and behavioral patterns that both security teams and communicators can use.
Do: Set up a Crisis Command Structure
Setting up a team ready to assess and respond to issues as soon as they arise should be a clear priority. Having an effective command structure ensures that each individual in the company is aware of their responsibilities to help manage the crisis.
Do: Communicate Transparently and Timely
Hiding a cyberattack can damage an organization on many levels. Communicators must inform internal and external stakeholders transparently and timely. When Home Depot fell victim to a data breach, hackers accessed credit card data belonging to 40 million customers. The court assigned to assess the legal consequences of the case considered the company’s response to be “responsible, prompt, generous and exemplary”. The US retailer had issued a press release, sent emails to customers and offered free identity theft insurance so timely that it mitigated their legal risks and liability resulting from the breach.
Don’t: Buy Back Your Stolen Data
Andrei Barysevich, a former director of a cyber intelligence firm, says there are cases where organizations try to buy back stolen data. Barysevich recommends not doing that as this creates an incentive for criminals to keep stealing more data. Instead, alert law enforcement officers and work alongside cybersecurity specialists to retrieve the data and restore access to compromised systems. US computer data storage company Spectra Logic applied this approach and successfully recovered from a ransomware attack.
Don’t: Take Too Long to Disclose Your Data Breach
Take Uber as an example. When the company fell victim to hackers that provoked a data breach back in 2016, they failed to reveal the breach instantly and instead disclosed it one whole year later. Such misconduct ended up costing the company a whopping $148M in legal penalties.
Wrapping Up
While the Dark Web may seem like an uncertain territory, companies and their communication teams must familiarize themselves with it. If 2021 has proven anything so far, it is more essential than ever to define and implement a viable security strategy. Starting with a competent risk assessment, securing access to key tools and insights, and informing an effective communication strategy will keep your organization, and its brand, intact.