All types of organizations increasingly depend on Threat Intelligence tools and insights. It comes as no surprise, therefore, that the Threat Intelligence market is projected to almost double from $11 billion in 2020 to $20 billion by 2027, corresponding to a whopping annual growth rate of 19%.
This growth mirrors the increasing number of cyber incidents organizations face and, at the same time, the challenges to building organizations that are more resilient to such attacks. While physical threats have always been there, fast-evolving cyber-enabled crimes have further complicated the equation.
Threat Intelligence provides essential context about threat vectors and threat actors to evaluate risks, tailor protection strategies, and inform decisions around network security, protection, and all aspects of organizational resilience, especially following an attack.
Why is Threat Intelligence Relevant?
Cybercrime is seen as “the greatest transfer of economic wealth in history” with annual costs estimated to reach $10.5 trillion by 2025 turning Threat Intelligence into a true lifeline for organizations.
The threat landscape evolves constantly and basic security measures are not sufficient to keep digital security teams up to date on cyber threats. Threat Intelligence helps security professionals understand the risks of advanced persistent threats, zero-day threats and exploits, an attacker’s thought process, motives, and attack behavioral patterns. Such insights enable them to learn tactics, techniques, and procedures employed by hackers, which, in turn, helps to improve the identification of attacks, and response times.
A global retail company decided to integrate Threat Intelligence components into their strategy and operations after increasingly struggling to filter out phishing emails. This move enabled them to gain contextual information, avert malicious attacks that were lurking online, and also helped save money considering that the average cost of cyberattacks is about $2.5 million.
Types of Threat Intelligence
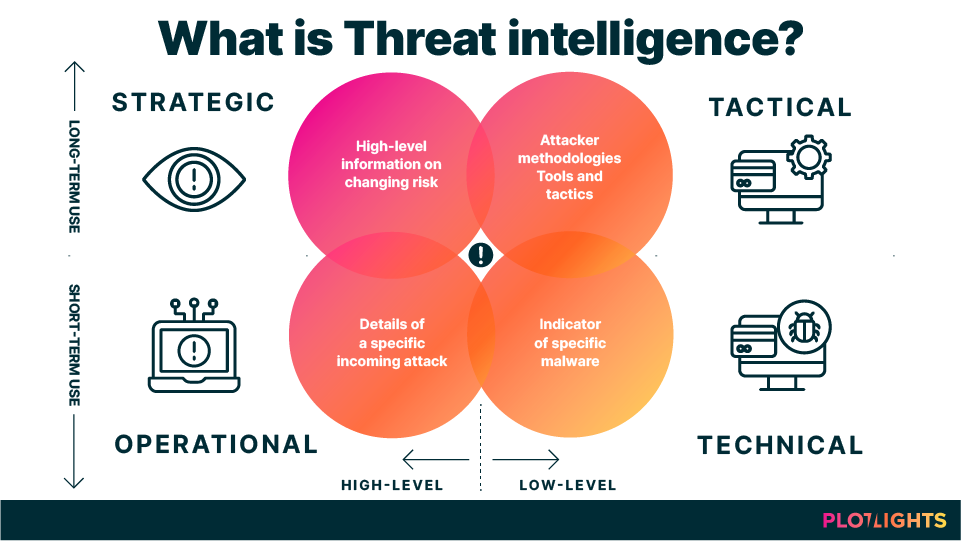
Typically, Threat Intelligence is organized into these categories: strategic, tactical, technical, and operational:
- Strategic Threat Intelligence is high-level intelligence, and it provides insight into cybersecurity also concerning real-life factors such as economic and political climates. Common topics are, for example, trends and patterns in threat actor tactics and targets as well as relevant geopolitical events. It is typically aimed at non-technical audiences, mostly decision-makers such as board members. These individuals are responsible for threat response, and it is, therefore, vital for them to know about the business impact of online risks and to comprehend emerging environmental patterns.
- Tactical Threat Intelligence, on the other hand, intends to cater to technical audiences who work in system and cybersecurity defense. This intelligence outlines how malicious actors operate (their techniques, tactics, and procedures). It involves tracking internal threat information feeds like network traffic data. Tactical threat intelligence allows security professionals to detect direct attacks on systems or understand prominent attack strategies.
- Technical Threat Intelligence refers to technical data about the tools and infrastructure threat actors deploy. Typical examples include subject lines or email content from phishing campaigns or maliciously registered URLs. So, if threat actors use business emails as a way into an organization (tactical info), the actual email subject lines used would qualify as technical Threat Intelligence.
- Operational Threat Intelligence indicates to cybersecurity teams how an unauthorized user executes a particular cyberattack. Using external sources, such as dark web forums, it gathers information directly from threat actors to piece together details such as timing, motives, and specific techniques.
Threat Intelligence Use Cases
The Threat Intelligence use cases combine physical and digital threat intelligence and leverage cutting-edge technology like machine learning to simplify processes. Here are some real-world applications:
Monitoring of Executives
Monitor the dark web and other aspects of the communication landscape for any risks that could negatively impact the safety, reputation, and data security of an organization’s executives, spokespeople, and other key personnel.
Fighting off Dark PR and Disinformation
Dark PR is on the rise and any activity that intentionally aims at negatively impacting organizations’ reputation should ideally be prevented. Use threat intelligence to identify strategic leaks of either classified or made-up material and any other strategic placements of fake content serving the specific purpose of harming organizations and their stakeholders. If that’s not possible, the forensic information that threat intelligence provides may be able to help repair the damage that’s done.
Security Triage and Operations
The sheer number of alerts makes it challenging to triage them manually, and this usually leads to “alert fatigue.” However, the right threat intelligence technology allows security teams to triage alerts, filter alarms, analyze incidents and attacks and act proactively.
Risk Analysis
As Threat Intelligence is contextual, it builds up strong risk models so that organizations can better assess risks and comprehend risk variables, assumptions, and results. It also enables businesses to effectively handle the frequency of attacks, exploitable vulnerabilities, and threat actors.
Vulnerability Management
By efficiently leveraging tools for Threat Intelligence, digital security teams can detect the vulnerabilities that pose significant risks to the organization. The purpose here is to identify real threats to avoid them altogether, or, minimize attack fallout.
Strengthen Security Posture
With Threat Intelligence, organizations can better understand the threat landscape in the long run, assess business risks, figure out mitigation strategies, make better investment decisions, and ultimately strengthen protection and security.
Fraud Prevention
Threat Intelligence also helps to prevent data compromises like leaked credentials and payment fraud. Furthermore, fraud prevention also raises warnings on typosquatting domains and phishing. Usually, cybercriminals leverage these to impersonate brands illegally and defraud users.
How Can Organizations Protect Themselves?
Threat intelligence is an extremely valuable asset for decision-makers looking to protect their organizations from threats. In addition, follow these best practices to mitigate the risks of cyberattacks even further:
- Install antivirus and firewall software as this is the first line of defense against malicious programs or actors from gaining access to your organization’s devices and network;
- Intensify email spam filters throughout the organization: research shows that in 2020, phishing attacks increased exponentially, accounting for one in every 4,200 emails, compared to one every 10,000 in 2019;
- Create a risk and crisis management plan including a crisis communication plan focused on minimizing reputation damage should the organization be hit by an attack. Data shows that more than 50% of marketing and PR experts see a fast and appropriate response as the biggest issue during a crisis — a risk and crisis management plan would provide a framework to tailor the best response promptly;
- Constantly scanning the environment for brewing risks using software, such as Plotlights, to either prevent attacks or inform post-attack communication activities;
- Last but not least, raise awareness and educate everyone involved, company internal or external, about the risks — crucial for any cybersecurity strategy to be effective. Just consider that 95% of data breaches are caused by human error.
Key Takeaway
The times for reactive security are long gone. The many recent examples demonstrate the risks coming with ignoring cyberattacks and call for proactive action. And that’s where Threat Intelligence-based strategies come in to protect organizations’ financial health and their reputation.