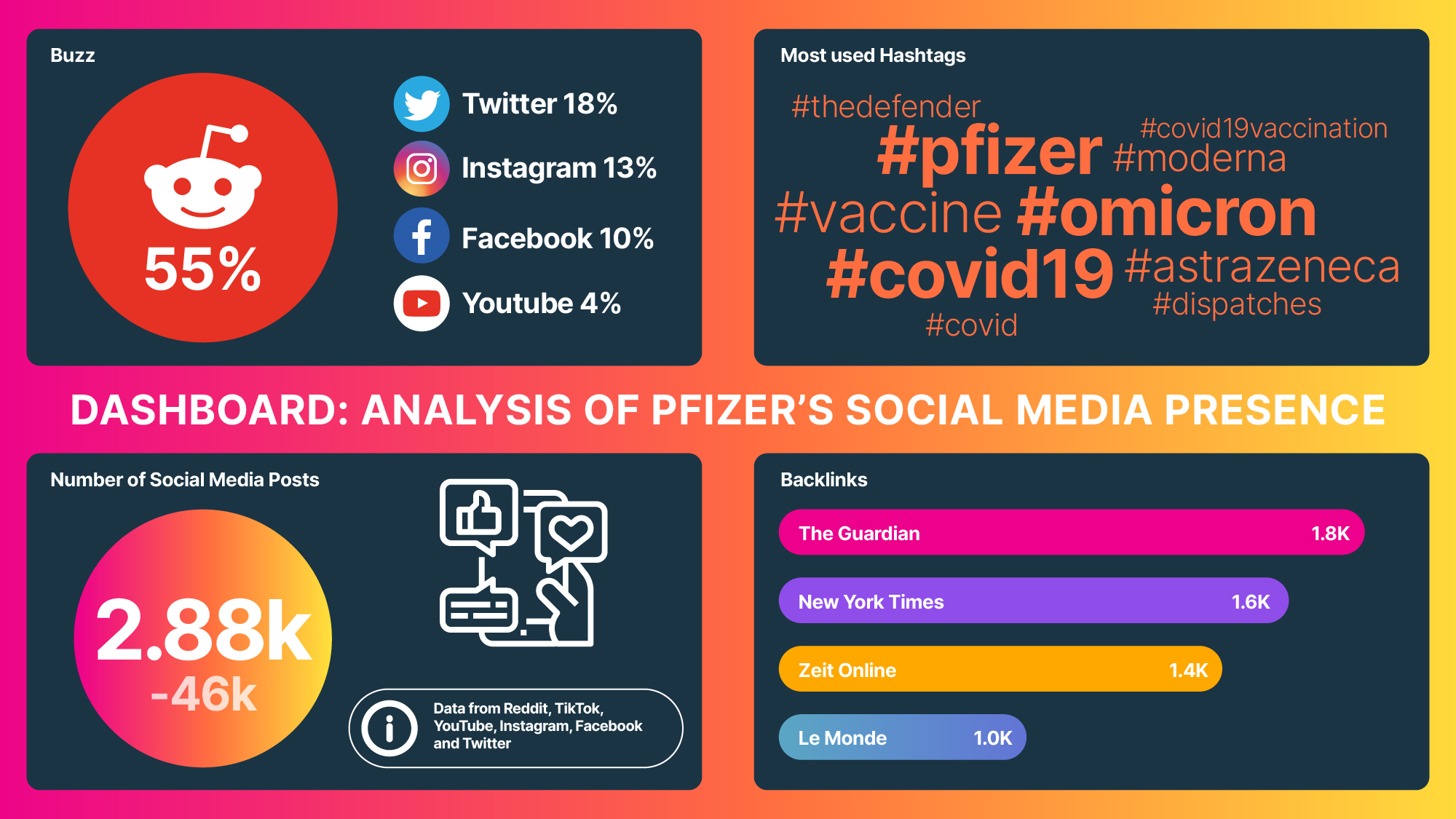
Cyberattacks are the number one non-COVID-19 risk to businesses worldwide. In 2021, ransomware attacks, in particular, continued to grow in numbers and business leaders across the globe asked communicators to step up and take on key roles in preventing, responding to, and recovering from such attacks.
In 2022 we expect the global threat landscape to further deteriorate which will directly implicate brands, communications teams, and agencies. That’s why Plotlights sat down with DarkOwl‘s CEO Mark Turnage to discuss relevant threat intelligence trends and what communications experts can do to keep their organizations, brands, and colleagues safe.
What Does DarkOwl Do?
DarkOwl is a dark web data provider and we offer the world’s largest known commercially-available database of dark web content in the information security industry. Utilizing proprietary AI-driven methodologies, DarkOwl enables organizations with near-real-time insight into an expansive set of dark web networks, including underground forums, authenticated chatrooms, and dark web marketplaces.
By making this data both accessible and searchable, DarkOwl makes it possible to monitor and gather intelligence specific to a multitude of use cases, such as corporate brand monitoring, cyber risk insurance intelligence, and identity fraud prevention.
Are Organizations Today Exposed to Higher Cybersecurity Threat Levels?
Yes, every company in any industry connected to the Internet is at risk. No one is immune to ransomware as a service or other targeted malicious cyber campaigns. The level of sophistication of threat actors is not what it was 5 to 10 years ago. The tools and techniques once reserved for cyber armies and nation-state actors are easily on the desktops of any hacker out there – regardless of their skill level.
Cybercrime is a profitable industry often fueled by threat actors’ discussions and malware circulated on the darknet. The fraud industry has skyrocketed, which has led to an increase in attacks against commercial websites and retail industries for the opportunity to exploit customer databases for personal information and consumer credit card data to conduct financial fraud. DarkOwl has witnessed an increase in discussions detailing attacks against point of sale and payment gateway systems. In addition to direct exploits to infiltrate the system itself, information stealer malware is required. Ironically, many ransomware-as-a-service groups rely on “infostealer” or “exfil” malware developed initially in support of the financial crime community to harvest critical sensitive information from their victim networks.
According to the World Economic Forum, ransomware has exponentially increased with researchers estimating an attack occurred every 11 seconds in 2021.
What Does the Current Cybersecurity Landscape Look Like?
The ransomware industry has shown explosive growth in 2021, and our analysts continue to observe these extortion-type services growing in both numbers and sophistication on the dark web — including associated communities such as criminal data brokerage and access as service providers.
Also, in recent years we have witnessed a response to society’s increased reliance on hyperconnected networks, and seen an increase in exploits against home networks, hybrid work environments, and exposed APIs.
We’ve also seen an increase in the development of cloud and enterprise-level malware, including deploying innovative attack methodologies against increasingly-complex interconnected supply chains and software dependence.
Traditional cyberattack methods have been augmented by increased computational processing, complex network proxies and botnets, and even eventually artificial intelligence. Curious technology and privacy enthusiasts in the darknet (often under the age of 18) are recruited for complex cyber offensive operations with geopolitical consequences. For example, Advanced Persistent Threats (APT) continue to threaten national security and critical infrastructure with complex attacks including malware served up via software updates, e.g. industrial espionage; crypto mining and distributed denial-of-service attacks employ increasingly pervasive botnets (including compromised mobile devices); business email compromise via targeted spear phishing, malware drive-by downloads, and social engineering has continued.
For political gain and financial influence, state-sponsored threat actors have not slowed their disinformation campaigns and foreign influence over research and development to poison public perceptions and developer trust.
What Best Practices Should Organizations Utilize to Protect Themselves?
An organization can protect itself against cyberattacks by implementing a comprehensive, cross-departmental security strategy coupled with a strong, company-wide communications program.
Employees should regularly undergo vigilant training to enable them to recognize and mitigate threats such as email spear-phishing attacks. It is also important to establish clear processes for when an incident does occur, including identifying key points of communication within the organization and a safe, trusting environment where employees feel comfortable coming forward.
Other, technical defenses against network compromise include:
- Implementing a zero-trust network architecture
- Shoring up commercial network defenses with up-to-date end-point security software
- Employing vulnerability management, and network protection systems
- Maintaining regular offsite backups
- Implementing network segmentation to reduce network traversal
- Regularly changing network credentials of employees’ passwords
- Implementing multi-factor authentication for all sign-in portals
- Monitoring the darknet for exposed credentials and mentions of the company on darknet forums and discussion groups.
Should Organizations Work Towards Becoming Cyber Resilient?
Yes, organizations should strive toward cyber resilience. CISA defines resilience as “the ability of an information system to continue to operate under adverse conditions or stress, even if in a degraded or debilitated state, while maintaining essential operational capabilities; and to recover effectively in a timely manner.” This definition typically refers to the information technology systems used by an organization, but the definition could be adapted to an “organization’s cyber resilience” in providing continuity of business under duress and quickly recover from disruption, for example, during a cyberattack.
This involves having a defensive security posture and mitigating risk where possible, including building a resilient network infrastructure, performing regular updates, setting up network segmentation to protect against DDoS and network intrusion, and monitoring threat intelligence feeds for potential brand or infrastructure risks.
What Skills Do Communications Experts Need to Have in This Environment?
Many communications experts face challenges when attempting to translate technical information into simple, digestible terms for non-technical audiences such as the general public, consumers, or indeed management. Turning simplified technical constructs into language that resonates across a range of diverse audiences is imperative for a comprehensive, security-oriented communications strategy. Here, the National Institute of Standards and Technology’s publication “Guide to Cyber Threat Information Sharing” is a great starting point.
Communications experts should also follow the advice of CISA, which recommends using the hashtag #BeCyberSmart to promote your involvement in raising cybersecurity awareness. There is also this great guide from CISA advising on external and internal communications.
How Should Organizations Communicate During or After an Attack?
The approach to strategic communications during or after an attack is highly dependent on the scenario, the target, and the degree of risk associated with the specific attack. In some cases, it is in the best interest of national security for a company or organization to not publicly disclose a security incident, which would involve purposefully perpetuating a misleading narrative in the interest of a larger defense strategy. In other cases, commercial organizations have seen success in deploying a highly transparent communications strategy in which they immediately release a public notice and communicate with all affected parties – including customers and other stakeholders – at each phase of the attack and remediation process.
Threat intelligence data plays an important role here as it provides communications professionals with a unique perspective and depth of analytical capabilities the opportunity to draw bigger pictures and formulate higher confident assessments & conclusions on what the reality of the cybersecurity space looks like. This includes both present risks and the likelihood of future outcomes.
Should Communicators Also Scan the Surface Web for Any Threat Intelligence?
While the dark web is one of many sources that should be leveraged to mitigate risks, there is also critical information available on the surface web. The level of organization and sophistication of malicious threat actors is far superior than we can imagine. They will implore anonymous and encrypted communication platforms to conceal sensitive information about victims and attack methodologies. These channels include chat platforms such as Telegram and Discord, as well as other end-to-end encrypted platforms such as qTox, wickR, and jabber. They also use direct messaging functionalities on darknet forums, where most public-facing forum content is likely being moderated and/or being monitored by law enforcement or threat intelligence researchers.
What Data Points Should Communicators Monitor?
Specific data points that organizations should monitor include:
- Domain and email domain exposure
- Specific emails exposure – especially for those with associated credentials
- Mentions of company name and brand assets
- Organization IP addresses
- Discussions of critical vulnerabilities that might be used to target the network architecture that is being employed by your organization.
Can You Name Key Cybercrime Trends in 2022 and Beyond?
Darknet threat actors continue solicitation for insider threats to aid in their cyber offensive campaigns. With the great resignation of the second half of 2021 and general dissatisfaction across several industries, we expect to see an increase in the number of insider threat-reliant cyberattacks.
Society’s reliance on the internet of things (IoT) at the individual and commercial level will be exploited in the near term. This could result in network intrusion, loss of sensitive data, and compromise of operations of critical infrastructure.
Disinformation groups will employ increasingly sophisticated deep fake video technologies supported by botnet-driven social media accounts to sow dissent and violence across western civilizations.
Information security specialists rely on artificial intelligence to detect malware in recent years, and we anticipate that AI techniques, such as deep learning will be used by threat actors to deploy malware capable of evading detection. AI-powered malware can be trained, with machine-learning methodologies, to conceal its identity, hide among common processes, and wait until a specific action occurs before deploying its malicious payload. Traditional rule-based security defense will have dramatically reduced effectiveness.
We also predict that there will be a rise in Killware, where malware is deployed to cause physical harm to the victim network or device. IoT-laden devices including autonomous vehicles are at increased risk of concerted attack and/or data corruption resulting in tragic accidents or loss of functionality. Killware as a cyber trend has been discussed in recent comments from the See U.S. Department of Homeland Security Secretary.
_________
 Plotlights thanks Mark wholeheartedly for this interesting interview.
Plotlights thanks Mark wholeheartedly for this interesting interview.
You can read more about the partnership between DarkOwl and Plotlights in this press release.
You can connect with Mark via LinkedIn or Twitter.
About DarkOwl
DarkOwl is a US-based cybersecurity organization that was launched in 2016. DarkOwl is a leading provider of Dark Web data, offering the largest commercially available database of Dark Web content in the world.